Contents
Notes
- This will NOT cover setting up Zitadel or FreeIPA from scratch, only the configurations required within the 2 applications to make them work together.
- Zitadel is managed via Terraform, will include code samples for setting up the app.
- FreeIPA can be managed via Ansible, Terrform providers for it do not yet have the required options for working with external IDPs.
- FreeIPA must be version 4.12 or greater.
Zitadel Application Terraform Code
locals {
oidc_apps = {
freeipa2 = {
project_name = "freeipa"
name = "FreeIPA2"
redirect_uris = ["https://master.ipa.REDACTED.co/ipa/idp/*", "https://ipa-ca.ipa.REDACTED.co/ipa/idp/*"]
response_types = ["OIDC_RESPONSE_TYPE_CODE"]
grant_types = ["OIDC_GRANT_TYPE_AUTHORIZATION_CODE", "OIDC_GRANT_TYPE_DEVICE_CODE"]
app_type = "OIDC_APP_TYPE_NATIVE"
auth_method_type = "OIDC_AUTH_METHOD_TYPE_NONE"
version = "OIDC_VERSION_1_0"
access_token_type = "OIDC_TOKEN_TYPE_JWT"
access_token_role_assertion = true
id_token_role_assertion = true
id_token_userinfo_assertion = true
}
}
}
resource "zitadel_application_oidc" "oidc" {
for_each = local.oidc_apps
project_id = zitadel_project.projects[each.value.project_name].id
org_id = zitadel_org.default.id
name = each.value.name
redirect_uris = each.value.redirect_uris
response_types = each.value.response_types
grant_types = each.value.grant_types
post_logout_redirect_uris = try(each.value.post_logout_redirect_uris, [])
app_type = each.value.app_type
auth_method_type = each.value.auth_method_type
version = each.value.version
clock_skew = try(each.value.clock_skew, "0s")
dev_mode = try(each.value.dev_mode, false)
access_token_type = each.value.access_token_type
access_token_role_assertion = try(each.value.access_token_role_assertion, false)
id_token_role_assertion = try(each.value.id_token_role_assertion, false)
id_token_userinfo_assertion = try(each.value.id_token_userinfo_assertion, false)
additional_origins = []
skip_native_app_success_page = try(each.value.skip_native_app_success_page, null)
}
```FreeIPA Configuration
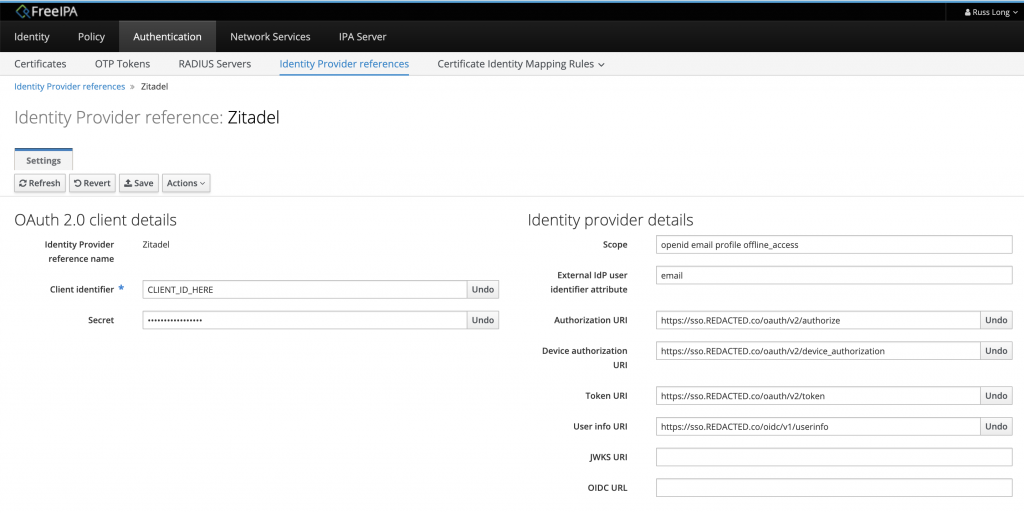
Go to Authentication -> Identity Provider References and add an IDP with the following.
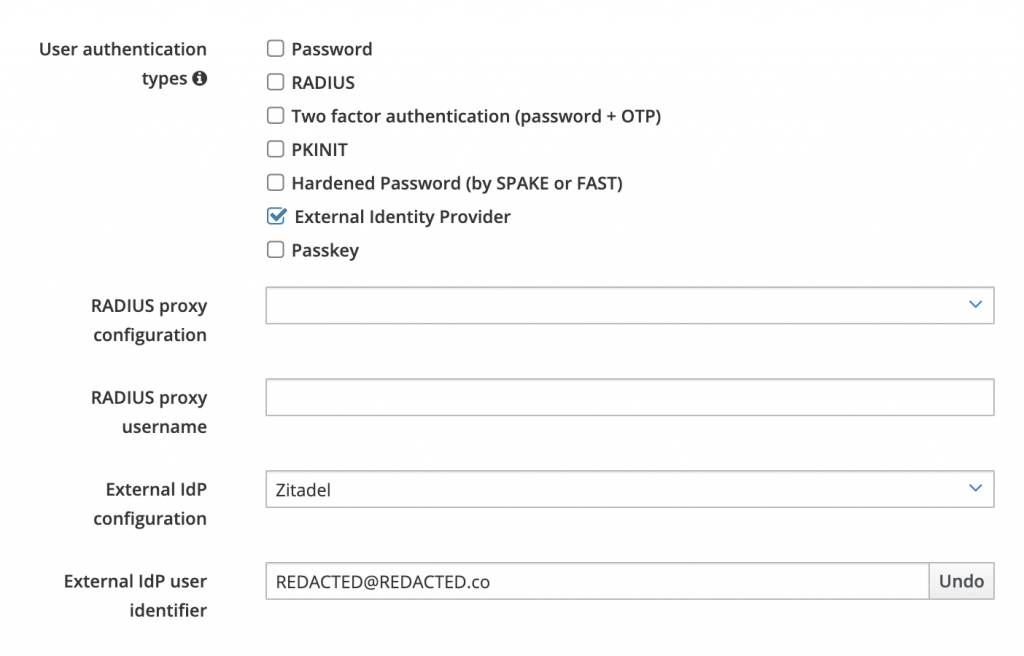
- For Users who need to auth against Zitadel, go to the user in FreeIPA Console, scroll Down to Auth Types, and set the options in the image below
SSH Experience
When users ssh to the server, they will be presented with a link in their terminal that they can either ctrl/cmd +click or copy/paste into a browser, once the auth flow in the browser is completed, the user can hit enter in their terminal, and they will be logged in.